

 |
|




























|
|
|
 |
|
|
2019 GLPS - Group LP Selfies
Your Team - Your Pride - Our Industry
Building Industry Pride - One Team Selfie at a Time
 |
Lowe's Region 6
Field AP Leaders
Following Delivery of AP University Courses...
"Training In the Trenches"
|

Pictured (left to right):
Larry Robbins, Doug Ginter, Paul Moore, Ben Fredbloom, Albert Latham, Jeremy
Roberson, Jay Adair, Ronda Fields, Jay Freeman
|
Lowe's Region 6 AP Team Members Always "Swinging for the Fences"
- Outside of Louisville Slugger Museum in Louisville, Kentucky
|

Pictured (left to right):
Jay Adair, Katrina Wiese, Jay Freeman, Ben Fredbloom, Jeremy Roberson, Paul
Moore, Albert Latham, Larry Robbins, Paul Richardson, Doug Ginter
Thanks to Albert Latham, Regional Asset Protection Director at Lowe's, for submitting
this GLPS.
|
 |
|
|
 
|
|
|
First Vendor Caught:
U.S. Security Manufacturer Selling Chinese Tech Claiming it's Theirs - $88M
Fraud
-Aventura Technologies Senior Management Charged with Fraud, Money Laundering &
Illegal Importation of Equipment Manufactured in China
-Security Hardware, Software & Peripheral Products Manufacturer on Long Island
 A
criminal complaint was unsealed in a Brooklyn federal court charging
Aventura
Technologies, a New York-based surveillance and security equipment company, and
seven current and former employees, with selling Chinese-made equipment with
known cyber security vulnerability to government and private customers,
while claiming the equipment was made in the U.S. Aventura has generated more
than $88 million in sales revenue since November 2010, and the charged
scheme has been going on since 2006, according to a Nov. 7 press release from
the U.S. Department of Justice. A
criminal complaint was unsealed in a Brooklyn federal court charging
Aventura
Technologies, a New York-based surveillance and security equipment company, and
seven current and former employees, with selling Chinese-made equipment with
known cyber security vulnerability to government and private customers,
while claiming the equipment was made in the U.S. Aventura has generated more
than $88 million in sales revenue since November 2010, and the charged
scheme has been going on since 2006, according to a Nov. 7 press release from
the U.S. Department of Justice.
 Four of the individual defendants are also charged with defrauding the U.S.
government by allegedly falsely claiming that Frances Cabasso was the owner
and operator of the company in order to obtain access to government contracts
reserved for women-owned businesses when Aventura was allegedly
controlled by her husband, Jack Cabasso. The Cabassos are also charged with
laundering the monetary proceeds of these fraudulent schemes. Four of the individual defendants are also charged with defrauding the U.S.
government by allegedly falsely claiming that Frances Cabasso was the owner
and operator of the company in order to obtain access to government contracts
reserved for women-owned businesses when Aventura was allegedly
controlled by her husband, Jack Cabasso. The Cabassos are also charged with
laundering the monetary proceeds of these fraudulent schemes.
Six of the defendants were arrested on Nov. 7. Law enforcement agents executed
search warrants at Aventura's headquarters in Commack, N.Y., and at the home of
Jack and Frances Cabasso. The government has also seized the Cabassos' 70-foot
luxury yacht, and has frozen approximately $3 million in 12 financial accounts
that contain proceeds from the defendants' alleged unlawful conduct.
securitymagazine.com
The Counterfeit Fight Continues
Ralph Lauren offers consumers a DIY counterfeit-checking tool
Ralph Lauren Corp. on Tuesday launched Digital Product Identities, which enables
consumers to use their mobile phones to verify the authenticity of Ralph Lauren
merchandise.
By scanning the Digital Product ID on the product label, consumers can confirm
whether their purchase is authentic, as well as learn about product details and
receive styling tips and recommendations. For Ralph Lauren, the technology
offers real-time visibility to track products from the point of manufacture and
improve inventory management.
The technology, developed in a partnership with EVRYTHNG, a connected IoT
platform, and Avery Dennison, is being phased into all Polo Ralph Lauren
products. "The application of this technology means every Polo product will be 'born-digital' which represents a new milestone in data intelligence innovation
in our sector," said David Lauren, Polo chief innovation officer, in a
statement.
The launch came the same day a CNBC investigation alleged that The RealReal
luxury resale site has been selling counterfeit goods and failing to properly
train those responsible for authentication
Start-ups such as Blockverify, Cypheme and Red Points have been gaining
attention for using artificial intelligence and/or blockchain and cloud-based
services to fight counterfeiting.
retailwire.com
CNBC Rips The Prima Donna of 'Authenticated Luxury Consignment' - The RealReal -
Counterfeits Slipping Through
RealReal's shares plunge as poor training
and tough quotas cast doubt on 'no fakes' pledge
 The
RealReal is an online luxury consignment store that differentiates itself by
saying everything is 100% real. The CEO has said there are "no fakes on our
site" and "every single item [is] authenticated." The
RealReal is an online luxury consignment store that differentiates itself by
saying everything is 100% real. The CEO has said there are "no fakes on our
site" and "every single item [is] authenticated."
CNBC spoke with nearly three dozen former employees and obtained internal
company documents that show not everything is authenticated by an expert and
employees work under strict quotas that lead to fakes being sold on the site.
CNBC read nearly 1,400 online reviews of the company and found that fakes,
damaged items and mistakes are top complaints.
The RealReal, which refused an interview, defended its authentication process
and said it has no tolerance for counterfeits.
The RealReal, launched in 2011, went public this year on June 28. That day, CEO
and founder Julie Wainwright said on CNBC's "Squawk on the Street" that "every
single item has already been inspected, authenticated before it gets on the
site." And in 2016, she told CNBC, "There's no fakes on our site."
This promise is key to the brand's identity: the idea that the company takes an
extra step to ensure items are authentic.
cnbc.com
The RealReal Defends Itself After CNBC Report on Counterfeits
"CNBC's report does not accurately represent the depth of our team's expertise
and the thoroughness of our authentication process. The RealReal has a rigorous
authentication process, it is core to what we do and central to our brand. We
make every effort to accurately authenticate the items we receive. If there is a
question about the authenticity of an item purchased from The RealReal, we will
always work with our customers to make things right. We stand behind both our
process and authenticity guarantee, and will continue to provide a safe and
reliable platform for buying and consigning luxury items."
In an email to customers Wednesday, The RealReal founder and CEO Julie
Wainwright appeared to back away from previous statements that there are no
fakes sold through its site. "This is a complex problem, and fighting global
counterfeiters is hard work. We strive for perfection, but may not be perfect
every single time," she wrote.
The missive follows an
investigative report from CNBC.
retaildive.com
The POS Transformation
The point-of-sale transformation continues
While there are many examples of POS advancement, a few specific specimens seem
to be generating the most excitement in the marketplace. These include:
Checkin-based transactions
Traditional checkouts - even self-service iterations - could soon become
antiquated thanks to the emergence of autonomous brick-and-mortar payment
technology. These solutions leverage sophisticated sensors, cameras and
machine-learning software to support genuinely frictionless purchasing
experiences. The autonomous checkout system that underpins Amazon's Go stores is
perhaps the most visible example here in the U.S.
Contactless credit cards
Credit and debit cards with contactless payment capabilities are commonplace
in economies across the globe. An estimated 50% of consumers in the European
Union use these payment methods, according to research from A.T. Kearney.
Adoption is even higher in Asia. In South Korea, for instance, 96% of shoppers
use contactless credit and debit cards. However, these items are essentially
nonexistent in the U.S., where just 3% of consumers use them. But experts
anticipate this will change - and soon.
Advanced POS hardware
As the retail industry evolves, so too does that POS hardware that makes
brick-and-mortar purchasing possible. Hardware developers had largely been
focused on making back-end improvements. But with
new shopper-POS interaction norms materializing, sellers and their technological
partners are now moving forward with more visible changes.
All-in-one POS assets are also rising to the fore, as more and more
sellers embrace the pay anywhere in-store concept and seek to equip
employees with everything they need to checkout customers, from card swipers and
pin-and-chip components to onboard receipt printers and cash drawers.
retailcustomerexperience.com
Understanding the Value in Autonomous Checkout
Convenience store retailers continue to grapple with how best to respond to the
disruption of frictionless checkout. I recently spoke with Crone Consulting's
CEO Richard Crone and Managing Partner Heidi Liebenguth for a podcast on
autonomous checkout.
 Crone
pointed out that Amazon Go is working at a 99.99% confidence level. "If
something does fail, from our estimations, somebody is reviewing the video on
the backend to see what actually happened and resolving the issue pretty
quickly," he said. Crone
pointed out that Amazon Go is working at a 99.99% confidence level. "If
something does fail, from our estimations, somebody is reviewing the video on
the backend to see what actually happened and resolving the issue pretty
quickly," he said.
"If you donate (your) SKU level data, dwell time and checkout data to
(autonomous checkout) startups, you're going to help build a unicorn value in
someone else's business while you're giving up the very essence, the most
prized asset of your merchandising concept," he said. "And that's your
SKU-level customer data while they're in the store."
Customer Identification
Liebenguth pointed out that the real value of the machine vision and machine
learning used in autonomous checkout isn't the autonomous checkout itself, but
gaining the data behind who the customer is through the check-in process.
"Check-in allows the retailer to personalize the customer journey through
the store, not waiting until checkout ...
It's important to recognize that Amazon Go is working from a clean slate
and not retrofitting frictionless checkout into an existing retail environment.
Amazon has essentially eliminated many of the exceptions found in
traditional retail that would pose challenges.
Another approach is scan and go, but some retailers are seeing shoplifting
with this approach.
"Another is order ahead, and this could be a replacement for self-checkout
altogether," Liebenguth said.
Data Capture
The advantage and value of autonomous checkout is in making the customer
experience more valuable and increasing visits and basket size.
Listen to the full podcast
here.
cstoredecisions.com
Combatting Shrink with Scan & Go
Many self-checkout theft tactics can be replicated with scan-and-go technologies
While self-checkout and automated solutions offer many benefits, there's a
perception they can also lead to greater theft. One survey of 13 major retailers
operating in the United States and Europe found
levels of stock loss were 1 percent in stores with self-checkout, compared with
0.67 percent of those with staffed checkouts.
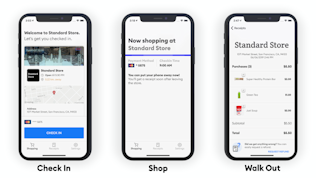
Although some loss can be attributed to mistakes on the part of the consumer,
self-checkout can expand opportunities for theft. Many common self-checkout
theft tactics, such as bagging items without scanning them or scanning
lower-cost items while bagging more-expensive ones, can be replicated with
scan-and-go technologies.
After expanding it to more than 100 stores,
Walmart ended its Scan & Go pilot after only a few months in May;
a former head of checkout innovation told Business Insider theft was a major
problem. At the time the program ended, Walmart said the program had low
adoption in addition to some of its own friction points "such as receipt checks,
weighted produce and un-bagged merchandise resulting from using the program."
Despite the concerns, the potential for shrink can be overcome with the right
optimization of staff and technology, says Jerry Sheldon, a retail analyst with
IHL. Spot checks by associates combined with new camera technology and AI can
also help retailers identify behaviors related to nefarious activities.
But in contrast to basic self-checkout, many of these new technologies can even
reduce theft and error, says Michael Suswal, COO and co-founder of Standard
Cognition. For example,
Standard Cognition's AI-powered autonomous checkout platform
can detect when someone is not logged into the system and it appears they are
about to leave the store with items they have not scanned. The system can then
alert associates about the issue.
When armed with the right information, associates can remedy the problem or
prevent the theft with non-confrontational questions, such as asking the person
if they need help downloading the app or if they were able to find everything
they were looking for.
Grabango, a Silicon Valley startup, can even charge potential shoplifters for
all items on their person, even if hidden from view at checkout or while leaving
the store.
As the system does the work, store personnel don't even need to confront
suspected shoplifters.
stores.org
C-Stores Represent the Canary in the Cage Type
Testing Ground
Appears to be Leading in the POS Transformation Process
Small enough to install, monitor and change almost instantly and has the numbers
of stores and transaction types necessary to truly test a large consumer base
quickly. Just an opinion.
What Not to Say in Written Communications
Phrases early-career professionals should avoid in work e-mail
 A
recent article in Forbes highlights the
importance of communication in the workplace.
A report from the World Economic Forum on the
top skills required for jobs in
2020 lists communication as one of the top 10.
And employers have identified communication skills as the
No. 1 trait they desire among recent graduates. A
recent article in Forbes highlights the
importance of communication in the workplace.
A report from the World Economic Forum on the
top skills required for jobs in
2020 lists communication as one of the top 10.
And employers have identified communication skills as the
No. 1 trait they desire among recent graduates.
E-Mail Tips
Keep in mind that when someone reads your message,
interpreting tone, intent and meaning is difficult. There are certain
phrases that should not be included in any message, including the ones listed
below.
"What specifically do you want?" - "I can't," "they can't," "it can't,"
"unfortunately we can't," "I don't," "we don't," "they don't" or "I am unable."
- "I've been in meetings."
"I am unavailable." - "This is too late." - "Do you have
... ?" "Can you ... ?"
or "You should." - "Let me know if there's a further issue." - "Dear [misspelled
name] ... " - "Are the results in?" "As I mentioned" or "like I said."
Use written communication to accomplish these four goals:
1. Build and maintain relationships.
2. Build your professional image.
3. Demonstrate consideration for others.
4. Share context.
shrm.org
"It's Not As Much What You Say
But What They Remember You Said Six Months From Now"
Gus Downing
6th Annual ISCPO Global Supply Chain Security Conference: Open For Registration
 The International Supply Chain Protection Organization (ISCPO) is pleased to
announce its 6th annual conference is
open for
registration at ISCPO.org. The conference will be held March 3-5, 2020 in
Dallas, TX where ISCPO members and loss prevention professionals will hear from
industry veterans and get the latest trends in supply chain security, industry
theft, global trends, and investigation. The International Supply Chain Protection Organization (ISCPO) is pleased to
announce its 6th annual conference is
open for
registration at ISCPO.org. The conference will be held March 3-5, 2020 in
Dallas, TX where ISCPO members and loss prevention professionals will hear from
industry veterans and get the latest trends in supply chain security, industry
theft, global trends, and investigation.
ISCPO's annual conference brings together loss prevention, security, and
protection professionals working within the global supply chain for two days of
networking, education, and collaboration.
iscpo.org
ROFDA to Join Forces with NGA
KKR Makes Formal Approach to Walgreens Boots on Record Buyout
Spin-off of Old Navy in doubt amid sudden departure of Gap CEO
Global Smart Supply Chain Summit 2019:
Technology Is Driving Improvement in the Efficiency of Supply Chains
UPS expects 26% jump in returns this peak season
Last week's #1 article --
Security Systems News Welcomes "40 Under 40" Class of 2019 Winners
Security Systems News is excited to bring you this year's inaugural
"40
under 40" class of 2019, made up of a diverse and talented mix of young
professionals representing the next generation of leaders in security.
Opening the award up to consultants for the first time added new depth and
perspective to this year's class, bringing all winners - consultants,
integrators, monitoring professionals and end users - together into one "40
under 40" class. Prior to this year, the award was called "20 under 40" and
included two classes, comprising 20 end users and 20 integrators. This year's
"40 under 40" class includes 14 end users, 11 integrators, 10 consultants and
6 monitoring professionals.
For a full list of all the winners, click here:
securitysystemsnews.com
In case you missed it --
KPMG: Online, mass merchants will grab biggest share of holiday purchases
Walmart turning its international money transfer service into a marketplace
Kroger is rebranding with a new logo and slogan

|
|

|
All the News - One Place - One Source - One Time
Thanks to our sponsors/partners - Take the time to thank them as well please.
If it wasn't for them The Daily wouldn't be here every day for you.
|
|
 |
|
 |
|
|
  |
|
|
PD: Gilbert couple arrested, charged with trafficking $2.7 million
in stolen property
According to Gilbert police, 42-year-old Zach
Robbins and his wife, 47-year-old Jie Robbins, were taken into custody at their
home near Warner and Higley roads on Friday. During the arrest and search of the
home, officers recovered around $500,000 - $750,000 worth of stolen over the
counter health and beauty products.
Police said they became aware of the operation about three months ago. Their
investigation revealed the Robbins' have been operating an interstate sales of
stolen property for more than four years. Detectives say the suspects
initiated sales through eBay and Amazon storefronts. The couple allegedly
paid others to shoplift items from local stores and then resold the merchandise
online.
Read more
For further information on PROACT, email inquiries to
PROACT@eBay.com. |
|

 |
|
|

|
|
S-TRON's Continued Salute to our Nation's Veterans

Pictured Left to Right:
Corporal Palacios, Marine Corps (4 years); Petty Officer 2nd Class Rosado,
Navy (8 years); Petty Officer 2nd Class Mattschull, Navy (8 years); Petty
Officer 1st Class Dunn, Navy (6 years); Private First Class McCory, Army
(3 years); Staff Sergeant Volk, Air Force (6 years); Not pictured: Petty Officer
3rd Class Benson, Navy (4 years)
On this Veterans Day,
S-TRON
is very proud to be a part of a Country and Community that honors those that
have put the United States of America before themselves. We understand the debt
of gratitude that Veterans are owed by us.
One of S-TRON's founding principles is recognizing and rewarding service,
whether on the battlefield defending our country, or in the support of our
community and customers.
The mission of our leadership team is to maintain a company and customer focus
based on this principle, so that we may "pay it forward" in a way that
demonstrates our commitment and gratitude. We are forever grateful for those
continuing to "Stand the Watch" and those who "Stand Relieved."
God Bless You, God Bless Us and God Bless America!
 ABOUT S-TRON ABOUT S-TRON
S-TRON is a National Electronic Security Solution Provider focused on exceeding
customer expectations. With a constant evolving offering, we provide new and
creative solutions and technologies to meet our customers everchanging
challenges.
"Standing by to Serve":
www.s-tron.com |
|
-01.png) |
|

|
|
Cybersecurity Workshop at NRF Big Show in NYC
Wednesday, January 15 / 8:00am - 1:30pm / New York Marriot Marquis
 This
workshop will provide retail business leaders and information security
professionals with strategic insights on cybersecurity threats and how they can
mitigate cyber-related risks to the retail enterprise through in-depth
discussions of the major cybersecurity challenges facing the retail sector.
This workshop is for retailers only and not open to press.
nrfbigshow.nrf.com This
workshop will provide retail business leaders and information security
professionals with strategic insights on cybersecurity threats and how they can
mitigate cyber-related risks to the retail enterprise through in-depth
discussions of the major cybersecurity challenges facing the retail sector.
This workshop is for retailers only and not open to press.
nrfbigshow.nrf.com
Sponsored by Deloitte
Removing a CISO After a Breach Is a Tough Call, Experts Say
Ousting an executive can sometimes do more harm than good, such as losing
valuable knowledge for the company.
A cybersecurity incident can put a stain on the corporate security chief, but
senior leaders must be sure that removing the executive doesn't further harm the
company, experts say.
The calculation involves evaluating whether the problem could have been
prevented as well as assessing the chief information security officer's
protection strategies. Data breaches will happen at some point for companies
that have valuable data. He said the question is whether the breach was
preventable or unpredictable.
Removing an executive after a scandal isn't unusual and it can help mitigate
financial fallout. "Investors do like to see firms taking action, doing
something to try to rectify or alleviate the situation," she said.
At a breached firm, the board and senior leaders should be sure the CISO was at
fault before moving to oust or demote the executive, she said. "It's not if a
breach will happen, but when, and it may not be anything the CISO did wrong."
High-profile breaches tend to trigger executive changes. Equifax Inc.
announced the retirement of its chief information officer and chief security
officer soon after disclosing a breach in 2017.
Firing a CISO after a high-profile security lapse can signal that the
organization takes data security seriously. But that can be a mistake, she
added: "When the CISO walks out the door, a tremendous amount of knowledge
leaves with them."
A more effective strategy, she said, is for the CEO to take accountability for
the lapse, allowing the CISO to focus on developing a tighter security program.
A survey of CISOs conducted by security firm Optiv Security Inc. in September
found that 58% said experiencing a data breach actually made them more
attractive to other employers. Around three-quarters of those surveyed said they
expected CISO roles to be a path to chief executive jobs in the future.
wsj.com
Insider Threats Hits Two
in 1 week
Security's Biggest Challenge
Trend Micro Employee Sold Consumer Data to Scammers
 A
Trend Micro employee stole and then sold contact information for 68,000 of the
company's consumer subscribers, which led to a raft of unsolicited tech
support scam calls, the company says. A
Trend Micro employee stole and then sold contact information for 68,000 of the
company's consumer subscribers, which led to a raft of unsolicited tech
support scam calls, the company says.
The employee has been fired and law enforcement has been contacted, the company
reports in a statement on its website. The employee accessed the data "with a
clear criminal intent,"
Trend Micro says.
The incident is an embarrassment for Trend Micro. It also highlights a problem
that is regarded as one of the most difficult computer security challenges: a
well-placed insider who decides to steal information from a company, or the
"insider threat." "Credit should be given to Trend Micro for being so open about
this issue," Honan says.
govinfosecurity.com
Feds Allege Saudi Spies Infiltrated Twitter
 The
U.S. Department of Justice has charged three men with perpetrating a campaign to
infiltrate Twitter and spy on critics of the Saudi government, and acting as
illegal agents of a foreign government. The
U.S. Department of Justice has charged three men with perpetrating a campaign to
infiltrate Twitter and spy on critics of the Saudi government, and acting as
illegal agents of a foreign government.
On Wednesday, prosecutors unsealed a
criminal complaint against two ex-employees of Twitter: Ali Alzabarah, 35,
of Saudi Arabia, and Ahmad Abouammo, 41, of Seattle. The complaint also
names Ahmed Almutairi, aka Ahmed Aljbreen, a 30-year old Saudi national.
Alzabarah has been accused of sharing 6,000 Twitter users' private details
with Saudi officials in 2015 and was arrested Wednesday in Seattle. While the
other two are back in Saudi Arabia. Abouammo Worked as Media Partnership Manager
in Seattle. Alzabarah Worked as Site Reliability Engineer (IT) in San Bruno,
Calif.
govinfosecurity.com
Twitter & Trend Micro Fall Victim to Malicious Insiders
Two separate incidents reported last week have once again highlighted how
insiders with legitimate access to systems and data can be far more dangerous
to enterprise security than external attackers.
"The premise of 'you can't deny what is granted' applies in that if an insider
has legitimate access, then it is difficult to determine if a behavior is
allowable," Poschman says. True intent can be hard to determine until after
damage is done because legitimate user behavior can often be erratic, he adds.
 Several tools are available to address insider threats, including user behavior
analytics and risk-based authentication products. Data-centric measures such as
tokenization and format-preserving encryption can also help by limiting access
to sensitive data for all users regardless of the permissions they have,
Poschman says. Several tools are available to address insider threats, including user behavior
analytics and risk-based authentication products. Data-centric measures such as
tokenization and format-preserving encryption can also help by limiting access
to sensitive data for all users regardless of the permissions they have,
Poschman says.
Terry Ray, senior vice president at Imperva, says trying to proactively restrict
all employees to just the data they need can be complex and even next to
impossible for enterprise security organizations. Even a zero-trust approach -
where every access request to a network or app is vetted for trustworthiness -
has limitations when it comes to malicious insiders, he says. "The only aspect
of zero trust that might have benefited Trend Micro would be least privileged
access - the idea that each individual should only have access to what they need
for their role," he says.
To be effective, insider controls have to be based on a continuous monitoring of
all user access to protected data. To spot unusual behavior, organizations need
to be constantly analyzing who accesses data, what they access, how they access
it, from where, and whether they should they have access to it.
"Monitoring user activity on corporate data is not only fully accepted, it's
assumed by employees," Ray says.
darkreading.com
Apple Card issuer investigated over credit algorithm gender bias claims
Goldman Sachs is facing a probe due to allegations that men are being offered
higher credit limits than women.
Last week, co-founder & CTO of Basecamp David Heinemeier Hansson published a
series of tweets calling Apple's new Card program "sexist." "Apple Card is a
sexist program," Heinemeier Hansson continued. "It does not matter what the
intent of individual Apple reps are, it matters what THE ALGORITHM they've
placed their complete faith in does. And what it does is discriminate."
As the Twitter thread gained traction over the weekend, Apple co-founder Steve
Wozniak chimed in, saying that the same thing happened with him and his partner.
The couple has no separate bank accounts, credit card accounts, or assets.
zdnet.com
Why Is Third-Party Risk Management So Complex?
 Organizations
should develop a comprehensive strategy for managing
third-party security risks and avoid over-reliance on any one tool, such as
vendor security risk assessment, monitoring or ratings services, says analyst
Jie Zhang of Gartner. Organizations
should develop a comprehensive strategy for managing
third-party security risks and avoid over-reliance on any one tool, such as
vendor security risk assessment, monitoring or ratings services, says analyst
Jie Zhang of Gartner.
Risk management professionals should use security risk resources carefully "and
you should really have your own strategy in terms of third-party risk," she says
in an interview with Information Security Media Group.
"For any organization today, third-party risk is a very messy area.
That's because there is no [dedicated] third-party risk organization in
general, within most organizations," she notes. "The risk ownership or
accountability is being shared among multiple functional areas within the
organization."
Too many organizations lack a centralized way of evaluating their vendors,
she notes. "So these third parties are coming to the organization from different
angles. There is no central role or program that is designed to go through all
these third parties from an intake process," she says.
Organizations that use the services of hundreds or thousands of third parties
"have to think about a
governance perspective," she says.
govinfosecurity.com
UPS, CVS Make First Residential Drone Deliveries of Prescription Medicines
Ring Flaw Underscores Impact of IoT Vulnerabilities
Getting Ready for the NIST Privacy Framework
Goodbye, Symantec for Consumers; Hello NortonLifeLock
|
 |
|
|

|
|
Critical Incident Management - Technology - Response
Pat McEvoy,
Sr. Dir of AP Administration, Hudson's Bay Company
Bryan Granata, Sr. Dir.
of Asset Protection, Hudson's Bay Company
|

|
With lone wolf terrorist attacks happening more frequently in the greater NYC
area and active shooter incidents increasing nationwide, the need for critical
incident management programs, technology and hardware has never been more
important.
Pat McEvoy, Sr. Director of Asset Protection Administration, Hudson's Bay
Company and Bryan Granata, Sr. Director Asset Protection, Hudson's Bay
Company, tell us about the preventative measures their stores are taking
from training drills and K9 dogs to gunshot detection systems.
|
Episode Sponsored By

|
|
|
|
 |
|
|
|
  |
|
|
More US retailers set to participate in Alibaba's Singles Day
The Nov. 11 Extravaganza is the Biggest Shopping Event of the Year
Alibaba's annual e-commerce extravaganza is about to begin. And as the Chinese
retail giant has courted more brands to participate, retailers around the world
are bracing for the biggest shopping event of the year.
Alibaba's Singles Day debuted on Nov. 11, 2009, as a day for those people not in
romantic relationships to celebrate themselves by shopping online. The
24-hour phenomenon trounces Amazon's Prime Day. In fact, it is expected to
generate more sales than the U.S. shopping holidays Black Friday and Cyber
Monday and spending on Thanksgiving Day combined, according to Adobe
Analytics.
Adobe, which checks the online transactions of 80 of the top 100 internet
retailers in the U.S., has forecast the five-day stretch from Thanksgiving to
Cyber Monday this year will bring in $29 billion in online sales. Alibaba's
Singles Day in 2018 did over $30 billion, and that number is expected to grow.
About 24% of U.S. retailers say they plan to run promotions for Singles Day,
Adobe said, after conducting a poll of 402 U.S. retailers that do annual sales
of more than $500,000.
cnbc.com
Alibaba Singles' Day Set to Challenge $31 Billion Record
Alibaba Group Holding Ltd. has logged more than 215 billion yuan ($30.7 billion)
of purchases during its Singles' Day bonanza, exceeding last year's record haul
about two-thirds of the way through its 24-hour shopping marathon.
bloomberg.com
Kount Introduces Industry's First Complete Solution for Criminal and Friendly
Fraud
US Holiday Sales to Cross $1 Trillion for First Time
Surveys: Online shoppers opt for Walmart over Amazon |
|

|
|
|
|

|
|
|
San Francisco, CA: Police arrest CEO, execs at East Bay business accused of
peddling stolen phones
 Police
arrested the CEO and top executives of a Hayward electronics business alleged to
have been buying phones stolen from cars and trucks in the Bay Area, and selling
them overseas, the Fremont Police Department announced Friday. Detectives said
they learned during a seven-month investigation that Torspin Wireless was
working with several street criminals to acquire stolen goods, including an
Oakland-based burglary crew that was stealing iPhones from FedEx and UPS trucks.
Authorities netted 1,800 stolen phones and large amounts of cash in a sting
operation that busted two California shops for buying and selling stolen
electronics.
sfchronicle.com Police
arrested the CEO and top executives of a Hayward electronics business alleged to
have been buying phones stolen from cars and trucks in the Bay Area, and selling
them overseas, the Fremont Police Department announced Friday. Detectives said
they learned during a seven-month investigation that Torspin Wireless was
working with several street criminals to acquire stolen goods, including an
Oakland-based burglary crew that was stealing iPhones from FedEx and UPS trucks.
Authorities netted 1,800 stolen phones and large amounts of cash in a sting
operation that busted two California shops for buying and selling stolen
electronics.
sfchronicle.com
Fuel-theft rings fill South Florida roads with 'moving bombs'
 These
criminals lug huge amounts of stolen gas across South Florida's roadways, hiding
hundreds of gallons in modified trucks and SUVs.. Authorities refer to the gas
thieves' converted trucks as moving bombs because of the hazard they pose if one
were to crash and explode. "They're out there, they're so common - trying to
blend with people who go to work every day," said Florida Highway Patrol Trooper
Alexis Otano. "God forbid one of these vehicles gets into an accident." And
officials say the gas theft has been on the rise. Such fuel pilfering cases
are up in Broward County, with 16 people charged so far this year compared with
10 last year. Between 2013 and 2017, only seven were charged.
sun-sentinel.com These
criminals lug huge amounts of stolen gas across South Florida's roadways, hiding
hundreds of gallons in modified trucks and SUVs.. Authorities refer to the gas
thieves' converted trucks as moving bombs because of the hazard they pose if one
were to crash and explode. "They're out there, they're so common - trying to
blend with people who go to work every day," said Florida Highway Patrol Trooper
Alexis Otano. "God forbid one of these vehicles gets into an accident." And
officials say the gas theft has been on the rise. Such fuel pilfering cases
are up in Broward County, with 16 people charged so far this year compared with
10 last year. Between 2013 and 2017, only seven were charged.
sun-sentinel.com
Santa Fe, NM: Burglars steal over $100,000 in Western style belt buckles and
jewelry from boutique
Vero Beach, FL: Woman switches tags to buy $1.8K in electronics for $3.70 at
Walmart
Natick, MA: Natick Mall Shoplifters used poncho to hide $650 of goods; Police
say 'brazen but sloppy'
West Monroe, LA: Housewife pays for 2 items at self-checkout, steals 44 (valued
at over $500), inside her purse is meth, pipe, scales and 26 Klonopin pills
|
|
|
|

|
|
|
|
 
|
|
Shootings & Deaths
Miami, FL: Shopping Center Security Guard accidentally shot, killed a 62 year
old woman
 Detective
Angel Rodriguez of the Miami-Dade Police department said the shooting occurred
shortly after 1 p.m. at a business is located inside the Seastone Shopping
Center. "Once the officers arrived, they discovered a female suffering from an
apparent gunshot wound," Rodriguez explained. "The preliminary investigation
revealed the victim was shot by an armed security guard stationed at the
business," Rodriguez said. "Investigators are interviewing the security guard to
determine the details surrounding the incident." Police did not immediately
identify the woman who was shot or the 54-year-old security guard.
miami.cbslocal.com Detective
Angel Rodriguez of the Miami-Dade Police department said the shooting occurred
shortly after 1 p.m. at a business is located inside the Seastone Shopping
Center. "Once the officers arrived, they discovered a female suffering from an
apparent gunshot wound," Rodriguez explained. "The preliminary investigation
revealed the victim was shot by an armed security guard stationed at the
business," Rodriguez said. "Investigators are interviewing the security guard to
determine the details surrounding the incident." Police did not immediately
identify the woman who was shot or the 54-year-old security guard.
miami.cbslocal.com
Boston, MA: Deadly, accidental mix of acid and bleach blamed for Buffalo Wild
Wings manager's death
 An
accidental mix of cleaners - acid and bleach - generated toxic fumes that killed
the manager of a Buffalo Wild Wings in Massachusetts, authorities said Friday.
The eatery's 32-year-old manager, Ryan Baldera, was killed and 13 others were
taken to the hospital, according to the Fire Department in Burlington,
Massachusetts, a Boston suburb. The accident occurred shortly after 5:30 p.m.
Thursday when a worker began cleaning the kitchen floor just before the dinner
rush. But that employee did not know that an acid-based cleaner, Scale Kleen,
had been spilled on the floor earlier, Patterson said. So when the worker used
chlorine- and bleached-based Super 8 on the floor, the mixture turned green and
started to bubble, Burlington Fire Chief Michael Patterson Patterson stated.
nbcnews.com An
accidental mix of cleaners - acid and bleach - generated toxic fumes that killed
the manager of a Buffalo Wild Wings in Massachusetts, authorities said Friday.
The eatery's 32-year-old manager, Ryan Baldera, was killed and 13 others were
taken to the hospital, according to the Fire Department in Burlington,
Massachusetts, a Boston suburb. The accident occurred shortly after 5:30 p.m.
Thursday when a worker began cleaning the kitchen floor just before the dinner
rush. But that employee did not know that an acid-based cleaner, Scale Kleen,
had been spilled on the floor earlier, Patterson said. So when the worker used
chlorine- and bleached-based Super 8 on the floor, the mixture turned green and
started to bubble, Burlington Fire Chief Michael Patterson Patterson stated.
nbcnews.com
Louisville, KY: Update: Kentucky Police Respond To An Active Shooter at Kroger
 The
man who allegedly fired at Louisville police officers outside of a Portland
Kroger on Thursday night before the officers fatally shot him has been
identified. Shelby Gazaway, 32, of Louisville, was pronounced dead at the scene
just after 6:20 p.m. Thursday, according to the Jefferson County Coroner's
Office. Dramatic police body camera footage released shows officers outside a
Louisville Kroger grocery store engaged in a shootout with a suspect who was
killed in the firefight. The man that was shooting inside the store came out and
started shooting at officers, they returned fire, killing that man.
courier-journal.com The
man who allegedly fired at Louisville police officers outside of a Portland
Kroger on Thursday night before the officers fatally shot him has been
identified. Shelby Gazaway, 32, of Louisville, was pronounced dead at the scene
just after 6:20 p.m. Thursday, according to the Jefferson County Coroner's
Office. Dramatic police body camera footage released shows officers outside a
Louisville Kroger grocery store engaged in a shootout with a suspect who was
killed in the firefight. The man that was shooting inside the store came out and
started shooting at officers, they returned fire, killing that man.
courier-journal.com
Otay Mesa, CA: Church's Chicken shooting victim remembered, mourned during
candlelight vigil
Newlywed Maribel Ibanez, 28, was killed when a gunman opened fire on employees
at a Church's Chicken Restaurant in Otay Mesa Wednesday evening. A family friend
said Ibanez was a newlywed and had been working at the Church's Chicken in Otay
Mesa for several years as a shift leader. Ibanez's friend said Ibanez took the
brunt of the gunfire when an unknown man walked into the restaurant at around
5:35 p.m. and shot at three employees across the service counter. The family
friend also identified the other two employees wounded in the restaurant
shooting: Mario Rojas and Humberto Ruiz. Police said Thursday that one of those
victims had been released from the hospital, while the other was still being
treated and was expected to recover.
sandiegouniontribune.com
Atascocita, TX: Jewelry store owner shoots suspects after smash-and-grab attempt
 Delton
Hayes looked out on the showroom of his jewelry store that was transformed in a
matter of seconds by a 4 person robbery crew. In the end, the store owner got
the last laugh, despite the damage. Mid-afternoon, a man tugged at the front
door of the store, which is controlled by a security buzzer. Moments later, four
robbers masked with bandanas rushed the store and hammered away at the glass
showcase. Hayes later learned two of them had been wounded. "One was shot in the
hand, according to a deputy. I shot the other one in the butt," he said.
abc13.com Delton
Hayes looked out on the showroom of his jewelry store that was transformed in a
matter of seconds by a 4 person robbery crew. In the end, the store owner got
the last laugh, despite the damage. Mid-afternoon, a man tugged at the front
door of the store, which is controlled by a security buzzer. Moments later, four
robbers masked with bandanas rushed the store and hammered away at the glass
showcase. Hayes later learned two of them had been wounded. "One was shot in the
hand, according to a deputy. I shot the other one in the butt," he said.
abc13.com
Update: University Park, TX: Pregnant employee shot during robbery CVS is
improving, along with her baby
Robberies, Incidents & Thefts
Kokomo, IN: Three arrested after alleged strong-armed robbery in Kokomo, three
county pursuit
 Three
woman were arrested after allegedly stealing UGG boots from the mall and leading
authorities on a chase in three counties. Kokomo Police Department officers were
called just before 5 p.m. Friday to the Markland Mall after mall security
officers said the woman stole UGG boots. One woman allegedly pepper sprayed a
security officer as he attempted to stop them. The vehicle they allegedly left
the mall in was later located by Howard County Sheriff's deputies, according to
the release. The suspects allegedly threw stolen property out of the window
during the pursuit. They were later stopped near Clay Terrace Shopping Center in
Hamilton County.
theindychannel.com Three
woman were arrested after allegedly stealing UGG boots from the mall and leading
authorities on a chase in three counties. Kokomo Police Department officers were
called just before 5 p.m. Friday to the Markland Mall after mall security
officers said the woman stole UGG boots. One woman allegedly pepper sprayed a
security officer as he attempted to stop them. The vehicle they allegedly left
the mall in was later located by Howard County Sheriff's deputies, according to
the release. The suspects allegedly threw stolen property out of the window
during the pursuit. They were later stopped near Clay Terrace Shopping Center in
Hamilton County.
theindychannel.com
North Phoenix, AZ: Man allegedly stealing diapers pulls gun on security guard
 The
Phoenix Police Department is asking for your help identifying a man who
allegedly stole diapers from a grocery store and pointed a gun at a security
guard. According to police, the suspect was last seen at El Rancho Market near
19th and Dunlap avenues on October 27 around 10 p.m. Police say the suspect
entered El Rancho Market and allegedly stole diapers, hiding them under his
shirt. When he was confronted by a security guard at the front door, police say
the suspect "pointed a semi-auto handgun from his front waist area and pointed
the gun at the victim before fleeing the store with the diapers.
abc15.com The
Phoenix Police Department is asking for your help identifying a man who
allegedly stole diapers from a grocery store and pointed a gun at a security
guard. According to police, the suspect was last seen at El Rancho Market near
19th and Dunlap avenues on October 27 around 10 p.m. Police say the suspect
entered El Rancho Market and allegedly stole diapers, hiding them under his
shirt. When he was confronted by a security guard at the front door, police say
the suspect "pointed a semi-auto handgun from his front waist area and pointed
the gun at the victim before fleeing the store with the diapers.
abc15.com
Pittsburgh, PA: Do It Best Home Center Shoplifter Flees Police In Broad
Daylight, Crashes Into Hillside
Englewood, OH: Three arrested in relation to Verizon robbery
Sentencings

|
Bentonville, AR: Man gets Life in prison for robbing Dollar General
Tracy Wright, 48, was found guilty Thursday night of aggravated
robbery and theft of property. The punishment for aggravated robbery is
usually 10 to 40 years or life imprisonment. Wright was charged as a
habitual offender, which meant he faced a mandatory life sentence
because of previous felony convictions. Wright had two previous
residential burglary convictions from Kansas. He also had a conviction
for battery on a law enforcement officer and a previous aggravated
robbery conviction. Bryan Sexton, deputy prosecutor, told jurors Wright
robbed the business with a toy gun.
arkansasonline.com
|
Cargo Theft
UK: Northamptonshire: Thieves steal cargo of Sex Toys worth over $1 million from
truck parked at roadside
|
|

|
| |

|
|

|
|
|
Daily Totals:
• 15 robberies
• 9 burglaries
• 0 shootings
• 0 killed |
|
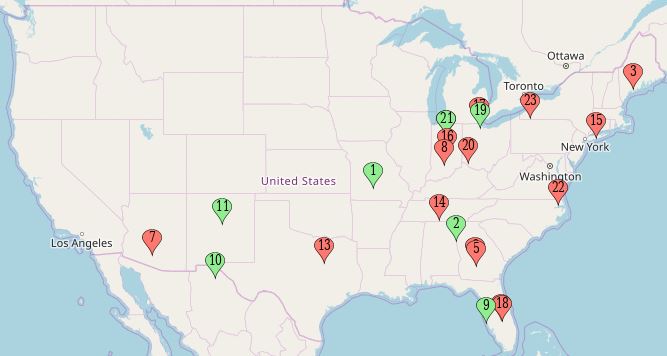
Click to enlarge map
 |
|
|
 |
|
|
|
|
Submit Your New Hires/Promotions or New Position
|
|
|
|
 |
|
|
 
|
|
|
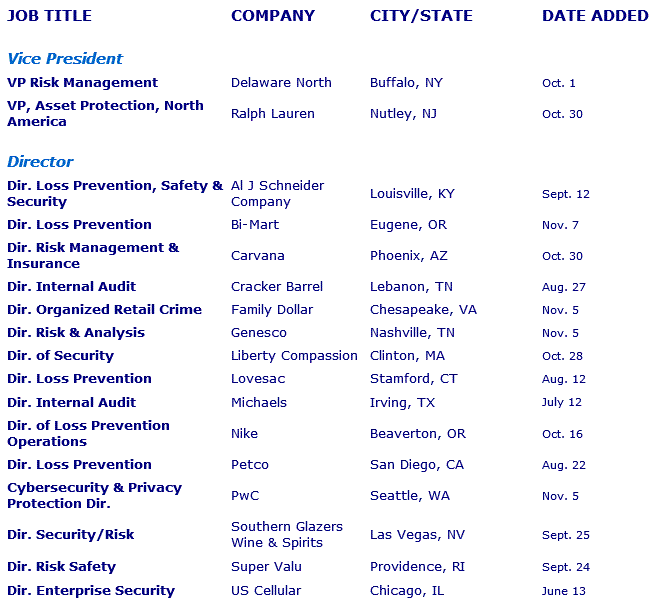
Featured Job Spotlights

|
Regional Loss Prevention Manager
Greater Toronto Area, Canada
Become the Newest Member of the VF Family. As the Regional Loss
Prevention Manager, you will have the critical function to support an entire
region of stores and serve as the subject matter expert in loss mitigation. You
will have the great responsibility to own and oversee all matters and
investigations of internal and external theft...
|

|
Senior ORC Investigator
Boca Raton, FL
The Senior Investigator is part of a fast-growing, ever changing environment
that partners with Store Operations to ensure we provide the best experience to
our customers. The Senior Investigator is responsible for assisting with
implementing a strategy to combat organized retail crime and external theft
across the TJMaxx and Marshalls brands...
|
 |
Loss Prevention Investigator
Seattle, WA
The Loss Prevention Investigator is part of a fast-growing, ever changing
environment that partners with Store Operations to ensure we provide the best
experience to our internal and external customers. With a focus on internal
cases, the Investigator takes complex investigations head-on through
establishing solid partnerships with store and LP leadership...
|
 |
Loss Prevention Investigator
San Jose, CA
The Loss Prevention Investigator is part of a fast-growing, ever changing
environment that partners with Store Operations to ensure we provide the best
experience to our internal and external customers. With a focus on internal
cases, the Investigator takes complex investigations head-on through
establishing solid partnerships with store and LP leadership...
|
 |
Area LP Manager
San Jose or Fresno, CA
The Area Loss Prevention Manager (ALPM) drives shrink improvement and asset
protection programs for two (2) to four (4) Districts which contain
approximately 25-65 Ulta Beauty Stores. The Area Loss Prevention Manager is
responsible to assess store procedures, promote awareness and methods to
prevent, protect and control losses...
|

|
Area LP Manager
Sacramento, CA
The Area Loss Prevention Manager (ALPM) drives shrink improvement and asset
protection programs for two (2) to four (4) Districts which contain
approximately 25-65 Ulta Beauty Stores. The Area Loss Prevention Manager is
responsible to assess store procedures, promote awareness and methods to
prevent, protect and control losses...
|

|
Regional Asset Protection Manager (North East)
Boston, MA
The successful candidate will be responsible for the management of the Asset
Protection function in their assigned area. Guide the implementation and
training of Asset Protection programs, enforcement of policies and procedures,
auditing, investigations and directing of shrink reduction efforts...
|
 |
Area Loss Prevention Manager
Charlotte, NC
Our Area Loss Prevention Managers ensure safe and secure stores through the
objective identification of loss and risk opportunities. Our Area Loss
Prevention Managers plan and prioritize to provide an optimal customer
experience to their portfolio of stores. They thrive on supporting and building
high performance teams that execute with excellence...
|
 |
Area Loss Prevention Manager
Seattle, Portland or Salt Lake City
Our Area Loss Prevention Managers ensure safe and secure stores through the
objective identification of loss and risk opportunities. Our Area Loss
Prevention Managers plan and prioritize to provide an optimal customer
experience to their portfolio of stores. They thrive on supporting and building
high performance teams that execute with excellence...
|
 |
Area Loss Prevention Manager
Calabasas, CA
Our Area Loss Prevention Managers ensure safe and secure stores through the
objective identification of loss and risk opportunities. Our Area Loss
Prevention Managers plan and prioritize to provide an optimal customer
experience to their portfolio of stores. They thrive on supporting and building
high performance teams that execute with excellence...
|

|
Loss Prevention Operations Specialist
Tucscon, AZ
The Loss Prevention Specialist will oversee the Burglar/Fire Alarm and overall
Physical Security function for stores including CCTV for all new stores,
renovations, acquisitions, closing, existing stores and warehouses. In addition,
this position supports the security/property control component for the Corporate
Headquarters main campus...
|
Featured Jobs
To apply to any of today's Featured Jobs,
Click Here

|
|
View Featured
Jobs |
Post Your Job
|
|
 |
|
|
|
|
|
|
|
  |
|
|
Networking has always been a key to career development and finding that next
job. However, if you're not careful it can also limit you, eliminate you and
even work against you. If your network is comprised of executives doing exactly
what you do, then you may have competition and may even find some working
against you. You've got to broaden and expand your network outside your
immediate group and establish relationships outside your company and your
professional circle. Remembering that quantity is no substitute for quality and,
as in any mutually beneficial relationship, what you bring to the table for them
is as important as what they bring to the table for you.
Just a Thought,
Gus

 |
|
We want to post your tips or advice... Click here |
|

|
|
|
|
Not getting the Daily? Is it ending up in your spam folder?
Please make sure to add d-ddaily@downing-downing.com to your contact list,
address book, trusted sender list, and/or company whitelist to ensure you
receive our newsletter.
Want to know how?
Read Here |
|
|
|
 |













-01.png)






















































 A
criminal complaint was unsealed in a Brooklyn federal court charging
A
criminal complaint was unsealed in a Brooklyn federal court charging





 A
recent article in Forbes highlights the
A
recent article in Forbes highlights the








 This
workshop will provide retail business leaders and information security
professionals with strategic insights on cybersecurity threats and how they can
mitigate cyber-related risks to the retail enterprise through in-depth
discussions of the major cybersecurity challenges facing the retail sector.
This workshop is for retailers only and not open to press.
This
workshop will provide retail business leaders and information security
professionals with strategic insights on cybersecurity threats and how they can
mitigate cyber-related risks to the retail enterprise through in-depth
discussions of the major cybersecurity challenges facing the retail sector.
This workshop is for retailers only and not open to press.

















































